The potentials of facial recognition
November 2, 2017
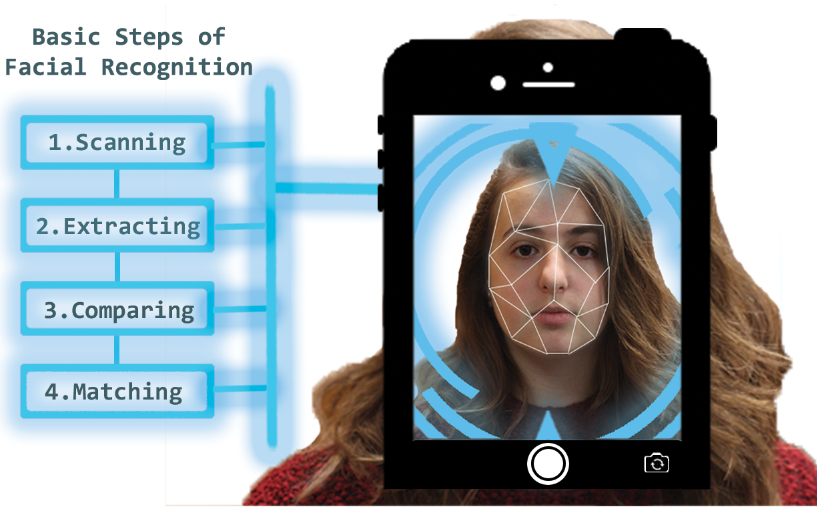
Holding the newly introduced iPhone X up to his face, Apple CEO Tim Cook lightly taps the phone screen. In a matter of milliseconds, the phone’s complex camera system projects over thirty thousand invisible infrared dots to identify the unique mathematical model of his face. The phone determines Cook’s face as a match to its stored unique facial map, and he gains access to the phone’s myriad of apps and notifications. In doing so, he has demonstrated the trademark feature of the iPhone X: facial recognition.
In its annual process of making significant changes and improvements to their newest smartphone models, Apple has replaced the traditional fingerprint-based Touch ID with a Face ID recognition system for the iPhone X, set to be released on Nov. 3. Similar to Touch ID, Face ID will be used to unlock the phone, log into certain applications and pay online. The iPhone X’s TrueDepth system, consisting of light projectors and sensors, takes several images of one’s face to extensively map one’s facial features in 3D. In order to account for poor lighting, a built-in flood illuminator produces invisible infrared (IR) light to allow the dot projector to determine a 3D landscape of one’s face using over 30,000 individual IR dot particles.
“I think facial recognition is definitely easier [than other login systems] — you don’t have to type anything or put your finger down,” said senior Avinash Jain, president of the Mobile and Web Development clubs. “I feel like we’re all used to putting our fingers down and we’re going to miss it, but then again, Apple was the first company to bring fingerprint [logins]. Apple is always taking the first step in [creating] something new, and I’m pretty sure Samsung and all the other phone companies are bound to follow.”
Although Apple’s recent feature has garnered a lot of attention, computer-based facial recognition softwares have been available for decades. As a matter of fact, the first facial recognition system dates back to the 1960s, when Woodrow Wilson Bledsoe developed a program to identify a face by calculating distances between prominent facial features. Since then, the Face Recognition Grand Challenge of 2006 has evolutionized facial recognition technology by creating algorithms that can more accurately determine a face in 3D by using high-resolution images and iris scanning. As a result, current facial recognition softwares can correctly identify a face in the dark, or if facial aspects change, such as growing a beard or wearing glasses.
“The future of facial recognition is bright,” said Anil Jain, a computer science and engineering professor at Michigan State University. “Cameras are everywhere, including surveillance cameras on street corners. So, there is a need to continue improving face recognition performance in ‘unconstrained’ situations and for person tracking.”
In addition to being incorporated in smartphones, facial recognition technology has been applied in a variety of fields. For instance, law enforcement officers have long relied on facial detection software to track criminals or identify threats in large crowds. Facial recognition has also been used for identifying missing children and catching shoplifters through security cameras. In 2000, Mexico used the same technology to prevent voter fraud in their presidential election, using facial recognition software to identify and compare pictures of voters in order to prevent individuals from placing multiple votes. Additionally, airlines such as China Southern Airlines and JetBlue are working on allowing passengers to pass airport security with facial scanning. In the United Kingdom, several schools have been implementing facial recognition softwares instead of traditional roll call systems to take attendance since 2009. Listerine, an oral health and dental care company, created an app that used facial recognition to detect when people were smiling at a blind person. The blind person would receive beeps and vibrations from a device if a smile was detected. Commonly seen in social media, facial recognition is used by companies like Facebook on uploaded images to speed up the process of tagging friends in pictures.
“I think facial recognition is very useful, especially in its uses for social media, such as tagging Facebook friends,” said junior Jason Dong. “Google Photos also uses facial recognition to recognize and label the people in your photos. I often use it to create personalized photo albums.”
Several modern technologies even use simple phone or computer cameras, instead of Apple’s multi-camera facial recognition systems, to authenticate facial features and movements. For instance, the mobile app ZoOm, which provides security for mobile banking and payments, employs a perception distortion, more commonly known as the fish-eye effect, to accurately validate a person’s presence.
“We are focused entirely at the moment on mobile authentication, not just recognition or identification; ZoOm authenticates by determining three-dimensionality and liveness of the correct user after it matches – or identifies – the correct user’s image,” said John Wojewidka, director of business development at ZoOm. “Other systems are better suited to recognition in circumstances like airports or municipal installation where a high-speed, high-volume face match for, say, a bad actor in a crowd is the goal. Or, they can be used to open a device or do very small transactions.”
Moreover, a greater emphasis has been placed on health and physiological benefits of facial recognition technology. Researchers at the National Human Genome Research Institute have found a way to use facial recognition technology to detect the DiGeorge syndrome, a disorder that can cause learning problems and heart defects and affects 1 in 4,000 children. Face2Gene, another facial recognition software, can inform doctors of the probabilities of a child having a certain genetic disorder. The largest advancement is facial recognition software being able to recognize genetic disorders in people of different ethnicities, as each ethnicity has unique facial features for genetic disorders.
Facial recognition software can also aid those who are paralyzed or have difficulty moving their fingers and arms. Rather than voicing commands or physically pressing computer keys, one can navigate computers and other devices by mere eye movement.
“At a hackathon, I saw a project where someone used facial recognition to check eye movement,” said Avinash. “For people who couldn’t move their hands, they created a desktop app where they could blink to click and blink twice to double click. It was really cool to see how they analyzed one’s facial movements.”
Nonetheless, facial technology continues to face several challenges regarding its reliability, security, privacy and other issues. Several facial recognition softwares contain algorithms that can cause it to more accurately identify a certain demographic of people. For example, in Anil’s 2012 study of mugshots from the Pinellas County Sheriff’s Office in Florida, the faces of women, African Americans and younger people were identified with consistently less accuracy. Additionally, the Government Accountability Office reported this June that the FBI’s facial recognition system has not been properly verified in terms of accuracy.
Although recent facial recognition softwares have improved their accuracy, hacking the system still poses a considerable challenge to most algorithm developers. Some experts have raised privacy concerns over police departments’ easier access to unlocking smartphones or other facial recognition login-based devices. A big difference between facial recognition and other forms of biometric data, such as fingerprints, is that facial recognition works at a distance. Therefore, one can use it without other people’s consent or knowledge. Unlike with Touch ID, Face ID allows police to simply hold one’s phone up to his or her face instead of forcing them to type in their passwords or touch the home button with their fingerprints. This allows law enforcement to identify potential criminals and terrorists without them knowing.
“You could definitely run into a lot of problems if [facial recognition] data gets leaked, because it makes up your identify, who you are, and everywhere people would be able to identify you and target you for ads,” said Avinash.
In addition, there was backlash from the general population after Facebook revealed its automatic tagging of friend in images through facial recognition technology. Many users complained that this was an invasion of privacy, prompting Facebook to change the default settings so that users could turn off the automatic tagging.
Facial recognition is readily available to most people, as any device fitted with a camera can take a picture for a facial recognition program to use. Fingerprints, on the other hand, always require a fingerprint scanner, often only found on select smartphones and scanners made by security companies.
“Maybe in future models, they will have multiple biometric recognition engines: face, fingerprint and iris,” said Anil. “The user can choose either one or for high security application; it may require all three [to login with] a fusion of the scores.”
Nevertheless, with facial recognition becoming the forefront in technological security, companies and facilities are increasingly shifting their screening and security toward more accurate biometric sensors and are working to address serious privacy and accuracy concerns. As advances in facial detection continue, however, the scenes featuring perfect futuristic technology shown in science fiction films and TV shows may soon become a reality.