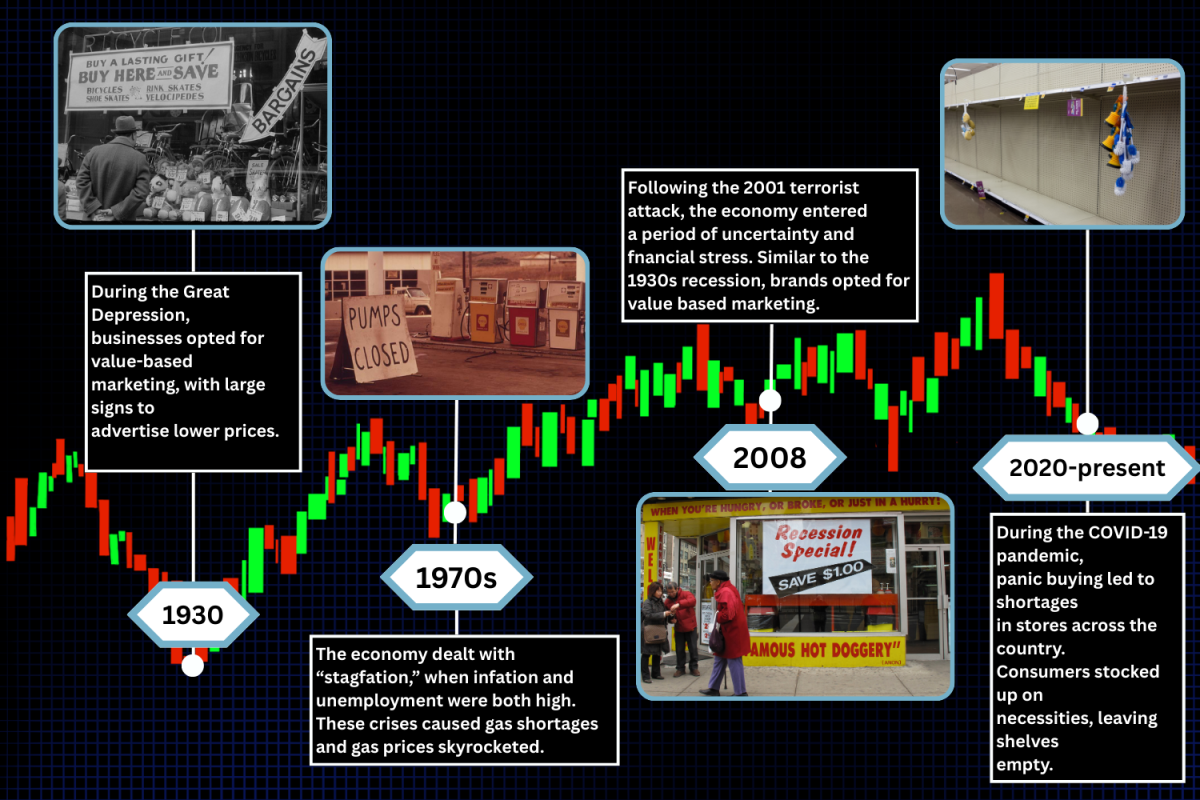
A layperson’s guide to malware and cybersecurity
Graphic illustration by Emma Constable
Security in the online world has become a serious threat, with many different types of malware being utilized to steal information or gain access to personal accounts.
November 9, 2021
June 2021: A ransomware attack shut down the Colonial Pipeline, the East Coast’s largest fuel supply line, for nearly a week. As critical infrastructure, personal information and databases rely more on storing and transmitting data online, there has been a sharp increase in malicious actors orchestrating cyberattacks. Security in the online world has become a serious threat, with many different types of malware being utilized to steal information or gain access to personal accounts.
Keylogger
Originally invented for employers to keep an eye on employees, keyloggers are a type of spyware typically downloaded from trojans that record and send a user’s computer keyboard inputs to a hacker’s database. Hackers then parse through the data with computer algorithms and deduce passwords and usernames. For example, algorithms look for the inputs after someone types “gmail.com” because they will usually be someone’s username and password. More advanced keyloggers can glean usernames and passwords to bank accounts, collecting banking, credit card and transaction data.
Trojan
On the surface, trojans seem harmless and look nearly identical to ordinary download links on websites or in emails. In reality, however, they are malware disguised as common computer applications. Used to transport all sorts of other malware, such as ransomware, spyware, backdoors and gateways for remote access, trojans can be found on both computers and smartphones. Short message service trojans are specifically designed to send and intercept text messages on mobile devices to steal personal information or send suspicious messages.
Rootkit
Rootkits encompass a family of clandestine programs that root themselves in the computer system and are very difficult to detect and remove. They are powerful enough to collect personal data or provide hackers remote access to devices while hiding the spyware’s presence. There are two main types of rootkits: kernel rootkits and user space rootkits. Kernel rootkits insert themselves into the heart of an operating system, fundamentally altering the system and concealing themselves from antivirus programs. From there, the malware allows hackers to collect personal data or install other forms of malware undetected. User space rootkits usually manifest as specific applications, such as a hidden extension on a web browser, and are generally easier to detect. But, they can still access personal information and crash browsers.
Malware Analysis
As the name suggests, malware analysis is when malware researchers study the nature of different types of malware. Static malware analysis involves reverse engineering the code in order to understand how the malware functions and find a cure. Dynamic malware analysis involves running the program in a sandbox environment where the malware is executed in a virtual space that does not affect the system. Then, malware researchers can observe the behavior and debug the code. More advanced malware analysis relies on artificial intelligence and machine learning to detect malware evolution, the process of malware code evolving to avoid security systems. Several studies in this field rely on powerful AI to find patterns in the code and detect new variants of malware.